Allion Labs/ Jackson Chen
Vulnerability Detection –Foundation of Systems Assurance
In the APP development process, information assets and risk management are quite important, but in fact, many companies have no testers or have non-professional testers. To save money, most companies are only focusing on the development of APP instead of testing the potential risks, which might lead to crash down after the APP goes online. The current common platform is Kali Linux, which includes several types of tools for users to use, but we are not limited to this platform, we can still use other tools to make the test more complete.
| Tools | Features |
| Kali Linux | Collecting information for web pages and apps,
Simulation vulnerability attack and vulnerability analysis |
| ApacheBench | Web and APP stress test |
| Nessus | Vulnerability analysis for the system |
Table 1 – Test Tools & Features
Test Platform

FIG.1 – Kali Linux
The system comes with a toolset. The Kali Linux system has 14 types of security tools and each category has different test tools. In the following article, 1) information collection 2) stress test and 3) vulnerability will be introduced.
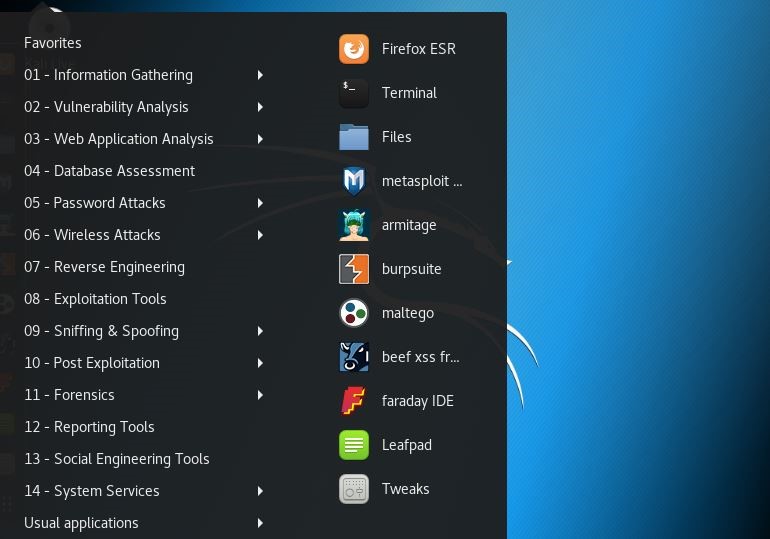
FIG. 2- 14 types of security tools in Kali Linux
1. Information Collection
Asset detection and information collection decide the probability you will find the security breach, therefore, the more target information is collected in the penetration testing, the better performance we can expect. To maximize the scope of the target collection and collect the information of subdomains and related domain names as much as possible are essential for our further vulnerability testing. The following is a practical example of information gathering.
I. The information needs to be collected:
-Hostname or IP and URL to be cracked
-The distinction is https or http
-The difference between returning information when login succeeds and fails
II.Tools
–Dnsenum for information collection in Kali Linux, and Hydra in password attack
III. Operation steps
-Using dnsenum to get the IP address of the target.
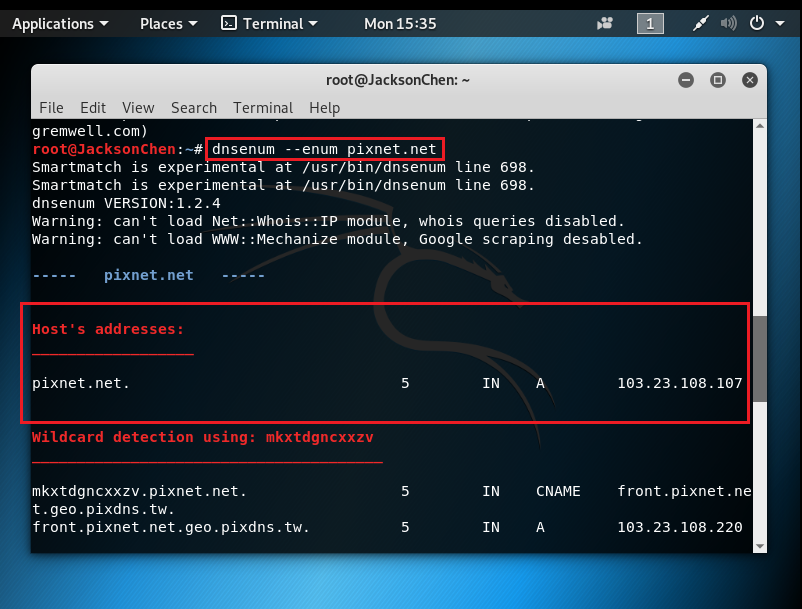
FIG. 3 – Get the Target IP Address
Hydra’s instructions
Hydra –l username –p password dictionary –t thread-vV –ip ssh
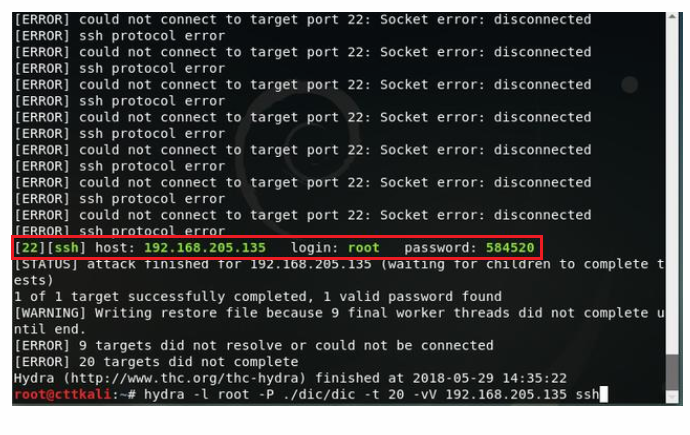
FIG. 4 – Get the Account Number and Password
Account:root Password:584520
IV. Solution
A. Dynamic login
Set up the limitation of the login time and the times of logins. For example, the effective duration of the annotation is 5 minutes, but the actual effective duration is about 30 minutes. There are restrictions on the number of times to obtain dynamic passwords, but no protection against password brute force is prevented, and the way to crack passwords is prevented.
B. Static login
Sessions are required to authenticate the registrant’s identity. Usually, after the user completes the identity authentication, the user profile will be saved, and then a corresponding set of ids is generated. This id must be unique, so it will be processed using the uuid mechanism.
C.Double verification
Now there is also a two-factor authentication method to protect the user’s account security. For example, if you log in to your Google account, you can set up login Security. Therefore, Google will send a text message with another login password or voice password, in this way it can enhance the security of the account.
D. The high password input frequency is prohibited
When the password input error of the same source exceeds a certain value, it should notify the system administrator by email or SMS immediately.
2.Stress test
Stress testing is very important in the design and development of large systems. Stress testing can help us discover system performance and evaluate system capabilities and perform targeted performance optimizations to help us verify system stability and reliability. In addition to Kali Linux, there are the following common tools:

FIG. 5 – ApacheBench
ApacheBench can easily simulate more than 1,000 users’ concurrent users testing, and the output test results are quite clear. Also, ApacheBench is not limited to the Linux operating system, you can install it on Windows. The following is a practical example of stress testing:
I. Tool
-ApacheBench
II. Operation steps
-Find out the Apache folder location.
-Execute ab.exe.
-As shown in Figure (9), the syntax is ab –n 100 –c 10 {url}.
FIG. 6 – Execute ab.exe in the stress testing
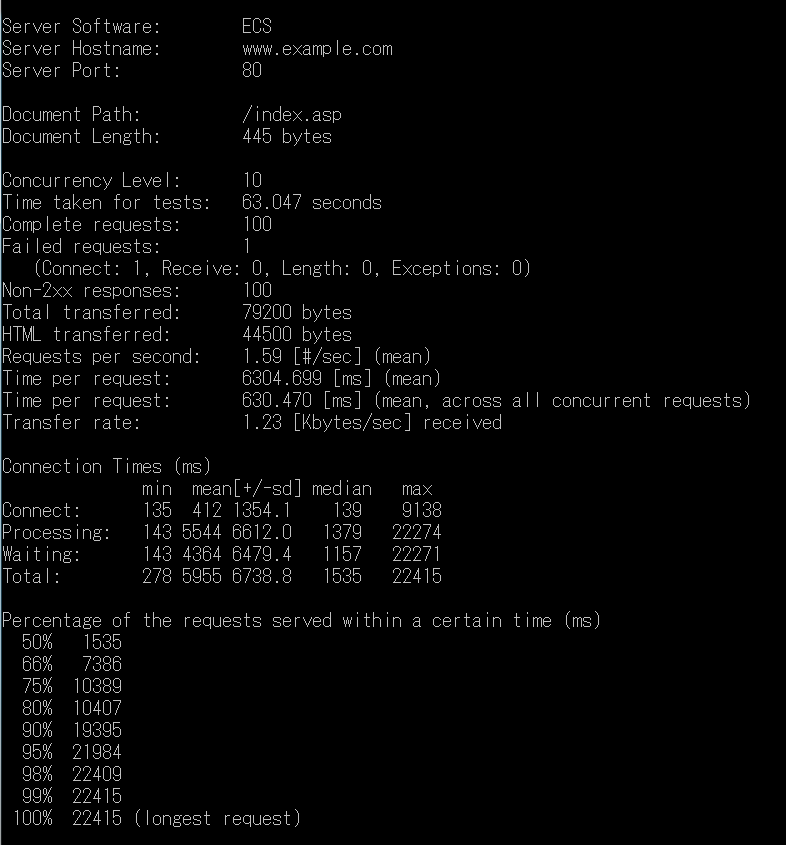
FIG.7 – Test results of stress testing
The fields are explained as follows:
Server Software: The operating system and version of the WEB host (if the web host settings turn off this information, no)
Server Hostname: IP address of the WEB host (Hostname)
Server Port: The connection port of the WEB host (Port)
Document Path: The path portion of the test URL
Document Length: The size of the page that the test page responds to.
Concurrency Level: Number of people who are simultaneously performing stress tests
Time taken for tests: the number of seconds spent on this stress test
Complete requests: Number of requests completed (Requests)
Failed requests: Number of requests (Requests)
Write errors: the number of write failures
Total transferred: The total amount of data transferred for this stress test (including the HTTP Header data is also included)
HTML transferred: The total amount of data transferred for this stress test (only the data of the returned HTML is calculated)
Requests per second: The requests per second can be responded to
Time per request: The average time spent per request (in milliseconds)
Time per request: The average time spent per request, the average of all simultaneous connections (in milliseconds)
Transfer rate: Network transfer speed from ab to Web Server
3.Vulnerability analysis
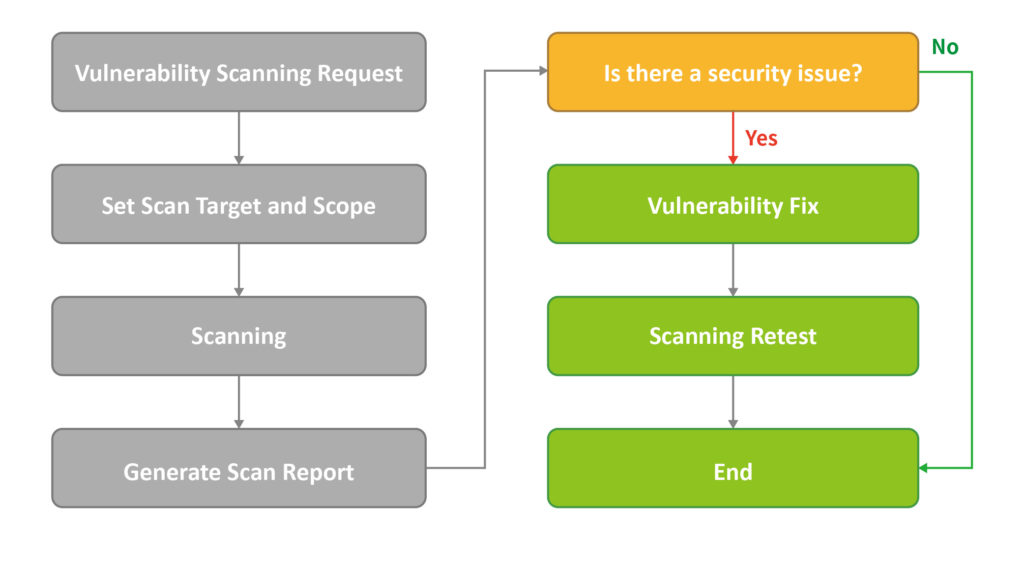
Vulnerability analysis refers to the process of quickly locating vulnerabilities in code, clarifying the attack principle, and accurately estimating potential exploit methods and risk levels. We will use the Nessus tool, which will help system administrators search for vulnerabilities in system hosts. Users can write attack test programs according to their own methods, and let system administrators make correct corrections and protections to system hosts. To avoid being attacked by intruders, the following is the vulnerability scanning process
I.Tool
-ApacheBench
II.Operation Steps
FIG. 9 – Nessus Initial Interface
- Log in
- Create or configure policies
- Scanning
- Analyze results and select configuration policies according to scanning requirements, which means vulnerability tests can be performed on targets.
FIG. 10 – Scan templates provided by Nessus
-Establish a strategy
-Named Local Vulnerability Assessment
-Target local address: 192.168.18.149
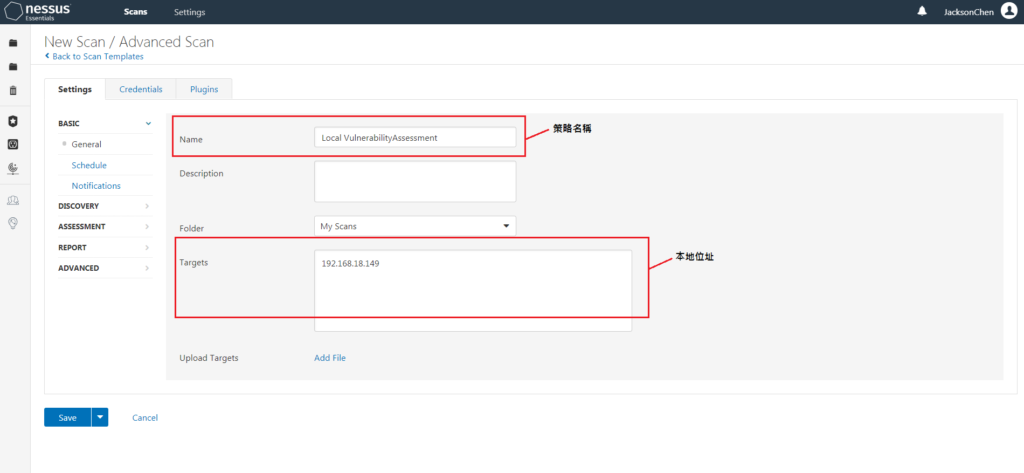
FIG.11 – Nessus establish strategy
FIG. 12 – Nessus Startup screen
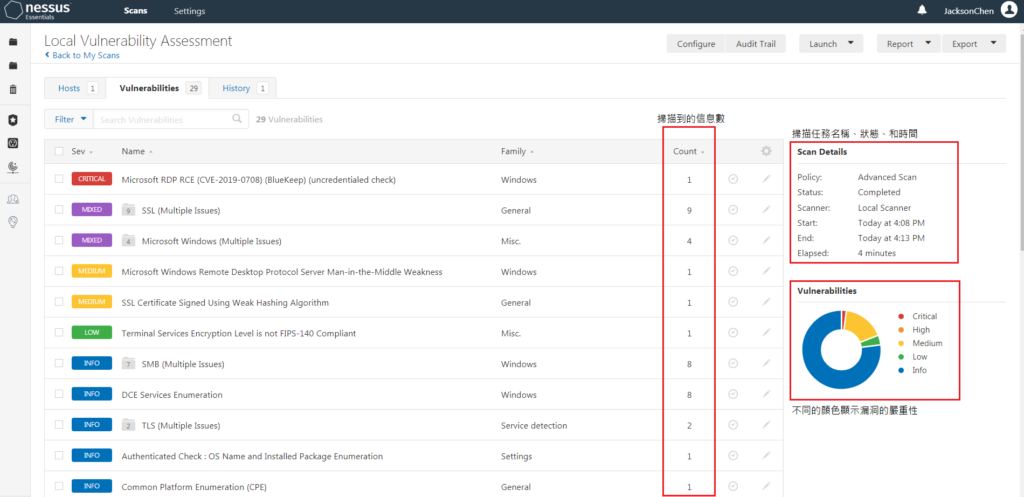
FIG. 13 – Scan results
Click on the vulnerability of the machine to view the detailed vulnerability information and provide a solution.
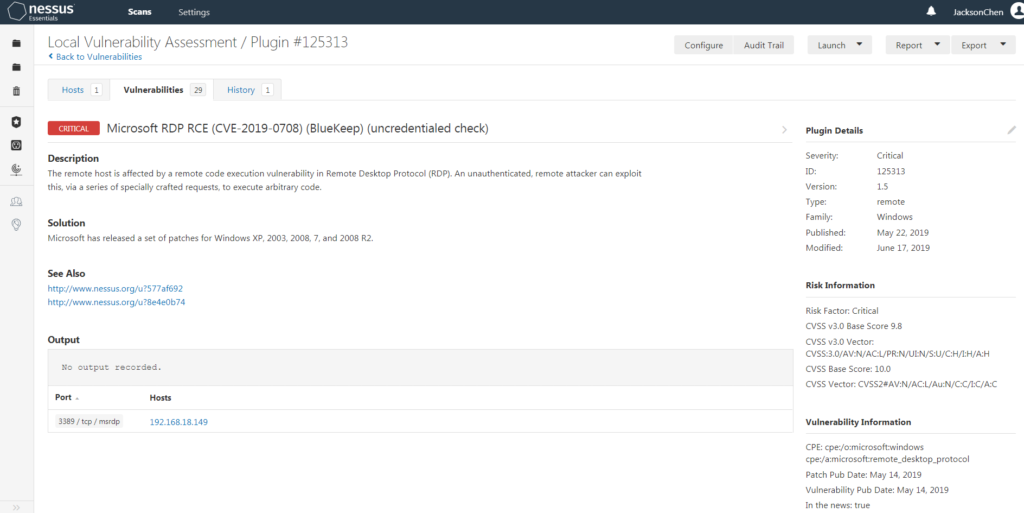
FIG. 14 – Situation of vulnerability
The vulnerability is described as: The remote host is affected by a remote code execution vulnerability in the Remote Desktop Protocol (RDP). A remote attacker without identity verification can exploit this vulnerability to execute arbitrary code through a series of specially crafted requests, or export a PDF file to provide a solution
One-stop Solution for Security Risks
For information security, web pages and apps, the following test scenarios are available:
- Security check
Review internal operations to provide suggestions for improvement and improve security protection
- Vulnerability detection analysis
WEB host or system to do security scans, providing results and assisting with corrections
- Stress test
WEB stress test. To check how many people can be online at the same time and the load capacity of WEB
Common problems
- Does the penetration test have a standard process?
Yes, it does. The following three penetration testing standard processes developed by several open-source organizations
OWASP (Open Web Application Security Project )
OSSTMM (Open Source Security Testing Methodology Manual)
PTES ( Penetration Testing Execution Standard )
- Is there no problem at all after the penetration test is completed?
Due to the hacker attack methods, even if the system does not make any changes, it is difficult to ensure that the future will not be invaded by new methods. Therefore, customers are still recommended to perform tests regularly.
- What is the difference between penetration testing and vulnerability scanning?
Penetration testing simulates the thinking of hackers in a manual way, conducts attack tests on the system, and compares the tester’s own experience and knowledge. Vulnerability scanning uses automated tools to detect the system and identify all known risks.
Getting Started with Allion Security Risk Detection
In the virtual world, the risk of security vulnerabilities is everywhere. Allion can simulate the hacking methods to conduct security detection on various systems, evaluate their risks and provide solutions. Allion provides customized security risk detection based on user scenarios and product features. Getting started with Allion security risk detection, with our comprehensive and diverse testing methods, potential problems of your products、APP and Web will be addressed. Besides, Allion also provides testing service for IoT products, please click: Information security of IoT wireless application: Is your smart device really secure?